Laboratorio de pruebas de VPN en oficina
Fecha: Noviembre 2010

Escenario: El escenario consiste en tres routers Cisco 800, un router Micronet SP880 y
simulando la nube de internet un Mikrotik RB433.
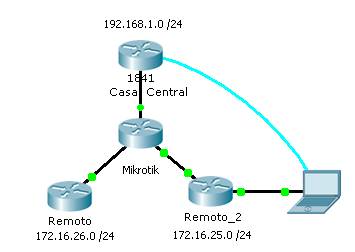
Direccionamiento de internet:
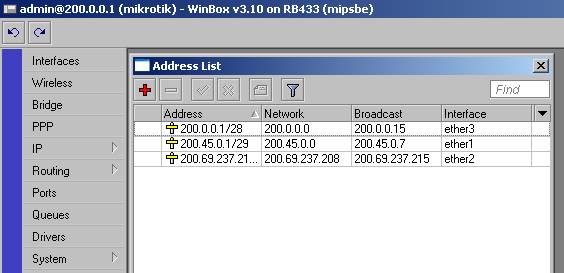
Configuración de equipos ( sólo
los Cisco):
CasaCentral#sh runn
Building configuration...
Current configuration : 1950 bytes
!
version 12.2
!
hostname CasaCentral
!
username admin privilege 15 password 0 cisco
username remoto password 0 Remot0
!
ip dhcp pool DHCP
network
192.168.1.0 255.255.255.0
default-router 192.168.1.1
!
!
crypto isakmp policy 10
hash md5
authentication
pre-share
lifetime 300
crypto isakmp key clave123 address 200.69.237.213
crypto isakmp key clave123 address 200.45.0.2
!
crypto ipsec security-association lifetime seconds 300
!
crypto ipsec transform-set 50 esp-des esp-md5-hmac
!
crypto map CMAP 10 ipsec-isakmp
set peer
200.69.237.213
set
transform-set 50
match address
100
crypto map CMAP 20 ipsec-isakmp
set peer
200.45.0.2
set
transform-set 50
match address
102
crypto map CMAP 30 ipsec-isakmp
set peer
200.45.0.3
set
transform-set 50
match address
103
!
interface Ethernet0
ip address
192.168.1.1 255.255.255.0
ip nat inside
!
interface Ethernet1
ip address
200.0.0.2 255.255.255.240
ip nat outside
crypto map
CMAP
!
ip nat inside source list 101 interface Ethernet1
overload
ip route 0.0.0.0 0.0.0.0 200.0.0.1
!
access-list 100 permit ip 192.168.1.0 0.0.0.255
172.16.26.0 0.0.0.255
access-list 101 deny
ip 192.168.1.0 0.0.0.255 172.16.26.0 0.0.0.255
access-list 101 deny
ip 192.168.1.0 0.0.0.255 172.16.25.0 0.0.0.255
access-list 101 deny
ip 192.168.1.0 0.0.0.255 172.16.24.0 0.0.0.255
access-list 101 permit ip 192.168.1.0 0.0.0.255 any
access-list 102 permit ip 192.168.1.0 0.0.0.255
172.16.25.0 0.0.0.255
access-list 103 permit ip 192.168.1.0 0.0.0.255
172.16.24.0 0.0.0.255
!
end
Remoto#sh runn
Building configuration...
Current configuration : 1516 bytes
!
version 12.2
!
hostname Remoto
!
username admin privilege 15 password 0 cisco
!
ip dhcp pool POOL
network
172.16.26.0 255.255.255.0
default-router 172.16.26.1
!
!
crypto isakmp policy 10
hash md5
authentication
pre-share
lifetime 300
crypto isakmp key clave123 address 200.0.0.2
!
crypto ipsec security-association lifetime seconds 300
!
crypto ipsec transform-set 50 esp-des esp-md5-hmac
!
crypto map CMAP 10 ipsec-isakmp
set peer
200.0.0.2
set
transform-set 50
match
address 100
!
interface Tunnel0
ip address
10.0.0.2 255.255.255.252
tunnel source
200.69.237.213
tunnel
destination 200.45.0.2
!
interface Ethernet0
ip address
172.16.26.1 255.255.255.0
ip nat inside
!
interface Ethernet1
ip address
200.69.237.213 255.255.255.248
ip nat outside
crypto map
CMAP
!
ip nat inside source list 101 interface Ethernet1
overload
ip route 0.0.0.0 0.0.0.0 200.69.237.212
ip route 172.16.25.0 255.255.255.0 Tunnel0
!
!
access-list 100 permit ip 172.16.26.0 0.0.0.255
192.168.1.0 0.0.0.255
access-list 101 deny
ip 172.16.26.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 101 permit ip 172.16.26.0 0.0.0.255 any
!
end
Remoto#
Remoto_2#sh runn
Building configuration...
Current configuration : 1633 bytes
!
version 12.2
!
hostname Remoto_2
!
username admin privilege 15 password 0 cisco
!
ip dhcp pool POOL
network
172.16.25.0 255.255.255.0
default-router 172.16.25.1
!
!
crypto isakmp policy 10
hash md5
authentication
pre-share
lifetime 300
crypto isakmp key 0 clave123 address 200.0.0.2
!
crypto ipsec security-association lifetime seconds 300
!
crypto ipsec transform-set 50 esp-des esp-md5-hmac
!
crypto map CMAP 10 ipsec-isakmp
set peer
200.0.0.2
set
transform-set 50
match address
100
!
interface Tunnel0
ip address
10.0.0.1 255.255.255.252
tunnel source
200.45.0.2
tunnel
destination 200.69.237.213
!
interface Ethernet0
ip address
172.16.25.1 255.255.255.0
ip nat inside
!
interface Ethernet1
ip address
200.45.0.2 255.255.255.248
ip nat outside
duplex auto
crypto map
CMAP
!
ip nat inside source list 101 interface Ethernet1
overload
ip route 0.0.0.0 0.0.0.0 200.45.0.1
ip route 172.16.26.0
255.255.255.0 10.0.0.2 (vía interfaz túnel, con esto
! logramos una malla completa)
access-list 100 permit ip 172.16.25.0 0.0.0.255
192.168.1.0 0.0.0.255
access-list 101 deny
ip 172.16.25.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 101 permit ip 172.16.25.0 0.0.0.255 any
!
end
Verificación: una vez generado el tráfico desde algún host en las redes
Internas se puede verificar la conexión de las VPN.
Remoto_2#
CasaCentral#sh crypto isakmp sa
dst
src state conn-id slot
200.0.0.2 200.45.0.2 QM_IDLE
1 0 (a Remoto_2)
200.0.0.2 200.69.237.213 QM_IDLE
9 0 (a Remoto )
!
! vemos que el destino es 200.0.0.2 ( este mismo router), lo cual
indica que
! el túnel se
originó en forma remota.
!
CasaCentral#
Remoto#sh crypto isakmp sa
dst
src state conn-id slot
200.0.0.2 200.69.237.213 QM_IDLE 3 0 (a CasaCentral)
Remoto#
Remoto_2#sh crypto isakmp sa
f_vrf/i_vrf dst src state conn-id
slot
/
200.0.0.2 200.45.0.2 QM_IDLE 1 0 (a CasaCentral)
Remoto_2#
Prueba
desde un host:
C:\>tracert 192.168.1.1
Traza a 192.168.1.1 sobre
caminos de 30 saltos como máximo.
1 1 ms 1 ms
1 ms 172.16.26.1 (no aparecen las IP públicas)
2 6 ms
6 ms 6 ms 192.168.1.1
Traza completa.
Verificación de las interfaces tunnel: ( estas, al contrario de los túneles IPSec, si aparecen en la tabla de enrutamiento )
Remoto#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile,
B - BGP
D -
EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 -
OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 -
OSPF external type 1, E2 - OSPF external type 2
i -
IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* -
candidate default, U - per-user static route, o - ODR
P -
periodic downloaded static route
Gateway of last resort is 200.69.237.212 to network
0.0.0.0
172.16.0.0/24 is subnetted, 2 subnets
S
172.16.25.0 is directly connected, Tunnel0
C
172.16.26.0 is directly connected, Ethernet0
200.69.237.0/29 is subnetted, 1 subnets
C
200.69.237.208 is directly connected, Ethernet1
10.0.0.0/30 is subnetted, 1 subnets
C 10.0.0.0 is directly connected, Tunnel0
S* 0.0.0.0/0
[1/0] via 200.69.237.212
Remoto#
(2010) Tales to sleep from uncle Ernest
Rosario,
Argentina